IdentityStore framework will automatically detect the configured WebLogic LDAP servers. Default is the internal WebLogic LDAP and this is also the first authenticator. You can also add other LDAP servers like Microsoft Active Directory or Oracle Internet Directory. For this you need to set the virtualize property with true as value to the idstore.ldap serviceInstance entry.
In this case I will set the AD Authenticator as first authenticator and don't use virtualize property, this way I can retrieve all the LDAP attributes and know for sure that new users are created in AD and not in the local WebLogic LDAP.
To create an user or change a password in AD we need to use LDAPS ( port 636 and not 389 ). Else you will get this error javax.naming.OperationNotSupportedException: [LDAP: error code 53 - 00002077: SvcErr: DSID-03190E49, problem 5003 (WILL_NOT_PERFORM), data 0 ];
The first step is to import the AD ca key and the AD public key to the local WebLogic TrustStore keystore.
keytool.exe -importcert -trustcacerts -alias ad_ca -file C:\2008-ca.cer -keystore C:\oracle\JDEV11~1.6\WLSERV~1.3\server\lib\DemoTrust.jks -storepass DemoTrustKeyStorePassPhrase
Trust this certificate? [no]: yes
keytool.exe -importcert -trustcacerts -alias ad_pub -file C:\2008-pub.cer -keystore C:\oracle\JDEV11~1.6\WLSERV~1.3\server\lib\DemoTrust.jks -storepass DemoTrustKeyStorePassPhrase
We also need to set the Hostname verification to None.
Create the AD Authenticator and also put all Control Flag to Sufficient ( also the default Authenticator )
Restart the Weblogic server and check if you can see all the AD users and the AD roles in the WebLogic Console .
Here is the java code to change the password of the AD user
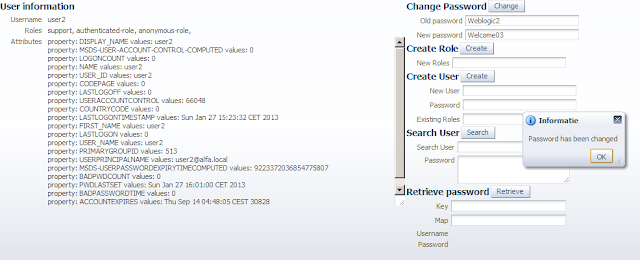
Here is the code to create an AD User with a password, add an AD role to this user and set the UserAccountControl to 66048.
Here you can download the demo application at github




