This blog is based on the article of Vikrant Sawant where he did the same with two WLS 9.2 Domains.I will use this blog as the starting point for my next blog entries, I am thinking about the following blog entries, How to use SSO / SAML with ADF Security , SAML with OWSM / OSB / ESB and BPEL. In this blog entry I will use the standard container security.
To make this work we need to have two WLS domains. I created a new domain with the configuration wizard of JDeveloper 11G and enabled the ADF option on this domain. I use the internal Weblogic domain of JDeveloper as the secondary domain.
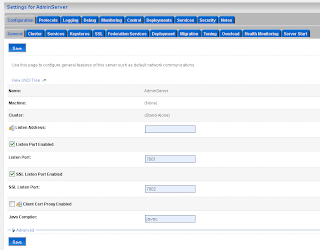
The new domain will be the SAML Source site but first we need to configure the WebLogic server instance by enabling SSL. SAML will need SSL for the secured communication between the SAML source and destinations domains. For this source domain I will use port 7001 and 7002 (SSL)
 Define the keystores, I have my own keystores but you can also use the WLS demo keystores
Define the keystores, I have my own keystores but you can also use the WLS demo keystores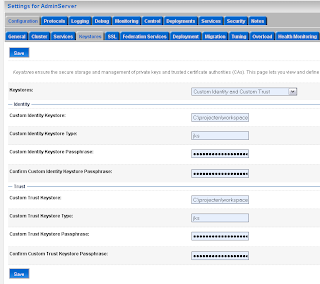
If you use your own keystore then you propably have to set the new private key alias.
 Add a SAML 1.1 source site at the Federation Services tab.
Add a SAML 1.1 source site at the Federation Services tab.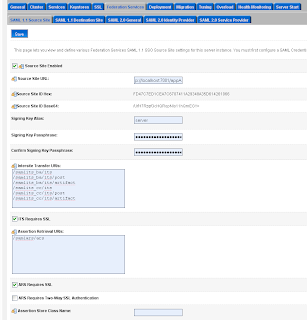 The second step on the SAML Source site is to configure the myrealm security domain. In this step we start by adding a Credential Mapping.
The second step on the SAML Source site is to configure the myrealm security domain. In this step we start by adding a Credential Mapping.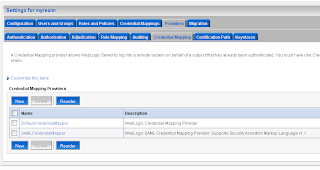 In the provider Specific Tab of the just created credential mapping we have to define the details.
In the provider Specific Tab of the just created credential mapping we have to define the details.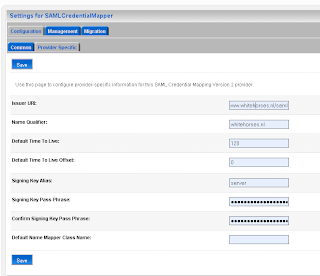
Now we can add the first SAML client (Relying Party ) of this source site. This will be the application which runs on the internal weblogic domain of JDeveloper. The first entry is called rp_00001
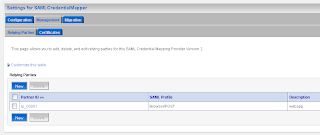 Add the url of secured page ( the url of the second application ) and the https port of the SAML destination url. Here we also have to provide the assertion id of the client SAML. This is APID=ap_00001. We will create this later (asserting party ) on the destination SAML domain.
Add the url of secured page ( the url of the second application ) and the https port of the SAML destination url. Here we also have to provide the assertion id of the client SAML. This is APID=ap_00001. We will create this later (asserting party ) on the destination SAML domain.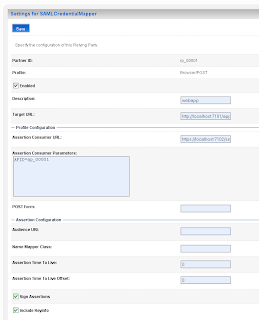 For the communication we need to import the public keys. In my case is this the ca and the server public key. Just export these key from the keystores and rename these keys to the der file extension.
For the communication we need to import the public keys. In my case is this the ca and the server public key. Just export these key from the keystores and rename these keys to the der file extension.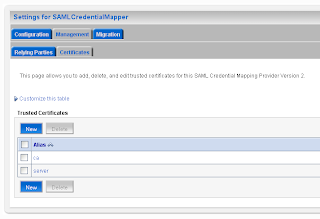
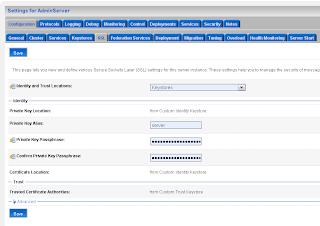
Step 3 is to setup the SAML destination site. I will use the internal Weblogic domain of JDeveloper for this. Default JDeveloper uses port 7101 and in this domain we also need to enable the SSL port ( port 7102 ).
Next go to the Federation Services of the server instance and enable SAML 1.1 destination Site.
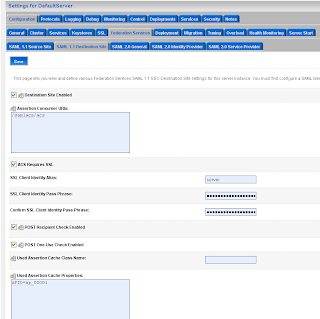 Go to the myrealm security domain and add a new SAML authentication.
Go to the myrealm security domain and add a new SAML authentication.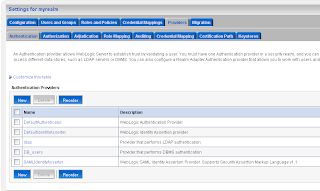 Add a new asserting party.
Add a new asserting party.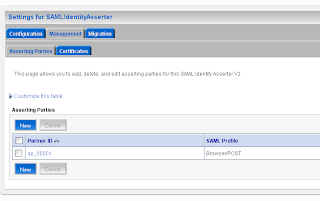 Here we add the url of the application which run on the source site. And the id of the relying party on the source site.
Here we add the url of the application which run on the source site. And the id of the relying party on the source site.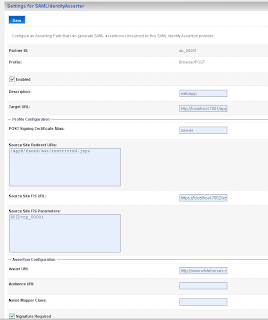 Here we also have to import the public keys of ca and server.
Here we also have to import the public keys of ca and server.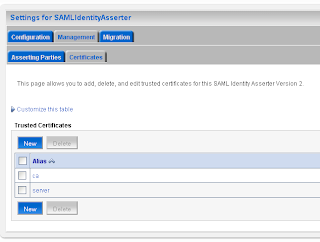 The last WebLogic step is to add a common authorization provider on both domains. I use a LDAP or a SQL authenticator for this. Both WLS domains need to have the same users and groups.
The last WebLogic step is to add a common authorization provider on both domains. I use a LDAP or a SQL authenticator for this. Both WLS domains need to have the same users and groups.We are finished with the WebLogic configuration. Now we can make two ADF applications. For these application I will use the faces-config.xml and not the unbounded task flow. And I use the standard container security and not ADF Security.
the web.xml of the source application looks like this.
<security-constraint>
<web-resource-collection>
<web-resource-name>aut</web-resource-name>
<url-pattern>/faces/aut/*</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name>valid-users</role-name>
</auth-constraint>
</security-constraint>
<login-config>
<auth-method>BASIC</auth-method>
<realm-name>myrealm</realm-name>
</login-config>
<security-role>
<role-name>valid-users</role-name>
</security-role>
the weblogic.xml of the source and destination application ( to map the valid-user role to the wls user group ).
<?xml version = '1.0' encoding = 'windows-1252'?> <weblogic-web-app xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.bea.com/ns/weblogic/weblogic-web-app.xsd" xmlns="http://www.bea.com/ns/weblogic/weblogic-web-app"> <security-role-assignment> <role-name>valid-users</role-name> <principal-name>users</principal-name> </security-role-assignment> </weblogic-web-app>
the web.xml of the destination application, now we have to use CLIENT-CERT.
<security-constraint>
<web-resource-collection>
<web-resource-name>aut</web-resource-name>
<url-pattern>/faces/aut/*</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name>valid-users</role-name>
</auth-constraint>
</security-constraint>
<login-config>
<auth-method>CLIENT-CERT</auth-method>
<realm-name>myrealm</realm-name>
</login-config>
<security-role>
<role-name>valid-users</role-name>
</security-role>
When the user logs in on the destination site then it will automatically redirected to the source site .
That's all for now.
Hi Edwin,
ReplyDeleteThanks for your post! It's very helpful!!!
I'm able to setup two applications and redirectly App1 to App2. However, I'm getting this error on the destination server:
Could not parse SAML response: org.xml.sax.SAXParseException: cvc-complex-type.2.4.c: The matching wildcard is strict, but no declaration can be found for element 'exc14n:InclusiveNamespaces'.>
Well done Jack,
ReplyDeleteyou are almost there. I got the same error , WLS tries to download the schema defined in the exc14n namespace.
WLS need to have a internet connection, then it works.
thanks
Hi Edwin,
ReplyDeleteI've got a workaround to not use internet connection.
Here's what I've done:
Under directory: $BEA_HOME$\modules, there's a file - com.bea.core.bea.opensaml_1.0.0.0_5-0-2-0.jar.
Make a change in this file:
com.bea.core.bea.opensaml_1.0.0.0_5-0-2-0.jar\opensaml\schemas\xmldsig-core-schema.xsd
At line 77, add processContents="lax" under the "any" tag so it reads like:
<any namespace="##any" minOccurs="0" maxOccurs="unbounded" processContents="lax"/>
This is a really good blog! And for those who has no easy internet access from WLS, this is a good workaround.
Regards,
Jack
Hi Jack,
ReplyDeleteThanks for the great workaround.
Edwin
Hi,
ReplyDeleteHow this SSO works when we have Weblogic cluster ?
Kuba
Hi Jakub,
ReplyDeleteI think you don't need saml in 1 domain. evertything is defined on the domain or the security realm so on every server in this domain should know the user.
I have never test this
WLS has built in identity propagation among domains - in fact there are two models. Global Trust and Cross Domain Security. For most cases, just use Global Trust.
ReplyDeleteIdentity propagation in this case is something like a web-application invoking an EJB in another domain.
If you're looking for cross domain SSO at the Web Tier, SAML is reasonable, but using something like Oracle Access Manager makes more sense.
The work around works well but this seems like a bug (or a feature?). In production servers may not have access to an internet connection. Are you aware of a solution in this scenario?
ReplyDeleteHi
ReplyDeletei was trying to do same on my side with WLS 10.3
i was using DemoIdentity keystore but
its giving error as
An error occurred during activation of changes, please see the log for details.
[Management:141191]The prepare phase of the configuration update failed with an exception:
SAMLBeanUpdateListener SAMLSingleSignOnServiceConfigInfoImpl: prepareUpdate() failed with exception: weblogic.security.spi.ProviderInitializationException: [Security:097558]FederationServicesMBean configuration Protocol Signing Key DemoIdentity is invalid.
Please suggest
Hi
ReplyDeleteI am also facing same issue which Gaurav is facing
Please help....
Hi,
ReplyDeleteCan you generate your own keystore by following this guide
download openssl and make a jks private keystore and a trust jks keystore
http://biemond.blogspot.com/2009/06/ws-security-in-osb.html
thanks
Edwin or anyone,
ReplyDeleteHow would you configure the Web apps for "virtual user" where you do not want to have the destination know the user only use the incoming assertion. I have been trying to configure that with no luck.
Ex-BEA dude
Hi,
ReplyDeletedon't know if that is possible maybe when you make a domain trust.
let me know if you made some progress
thanks
Hi...
ReplyDeleteI am facing Error 403---Forbidden with SAML authentication. Please help...
Hi
ReplyDeleteCan you give me your wls settings of the two servers.
Thanks Edwin
Edwin,
ReplyDeleteI have followed the steps by Vikrant Sawant for WLS 9.2, but tried to use 10.3 insead. Settings are same as 9.2
Thanks...
Hi
ReplyDeleteCan you send me the config.xml of your two wls servers.
biemond at gmail dot com
thanks
This works fine for SAML 1.1; however, there is a huge difference between SAML 1.1 and SAML 2.0. Have you attempted to configure SAML 2.0?
ReplyDeleteHi,
ReplyDeleteMade a new blog how to do this with SAML2
http://biemond.blogspot.com/2009/09/sso-with-weblogic-1031-and-saml2.html
thanks Edwin
Hi Edwin,
ReplyDelete1) In the previous post sukhveer,
sukhveer said...
Hi...
I am facing Error 403---Forbidden with SAML authentication. Please help...
Did you get to the bottom of his problem ?
2) I am using wl10.3 as well and followed Vikrant's tutorial. I can login for appA but I can't go to appB, I get an issue with my certificate and all. Any idea how to create trusted certs and key ?
Hi
ReplyDelete1) In the previous post sukhveer,
sukhveer said...
Hi...
I am facing Error 403---Forbidden with SAML authentication. Please help...
Did you get to the bottom of his problem ?
yep it was a keystore problem and very important are the hostnames, don't mix localhost and the server name
2) I am using wl10.3 as well and followed Vikrant's tutorial. I can login for appA but I can't go to appB, I get an issue with my certificate and all. Any idea how to create trusted certs and key ?
You generate your own keystore by following this guide
download openssl and make a jks private keystore and a trust jks keystore
http://biemond.blogspot.com/2009/06/ws-security-in-osb.html
thanks
How would you accomplish this with a load balancer (ex. F5) or web server (Apache) in front of the Weblogic Servers? Since you have to provide the target and source URLs in the Security Realm section this doesn't seem to be intuitive if you have multiple servers in the pool. Please let me know your thoughts.
ReplyDeleteHi,
ReplyDeleteusing apache should also work , just use the apache address instead of the wls server address.
thanks
Thanks for ur post,it was v.helpful.
ReplyDeleteOur Set up for weblogic works as suggested by vikrant,but my application call ceratin module (Oracle ADF)from OAS10g,I know we can implement SAML on apache.I'm not finding any documentaion for that ,do u have any info.
Thanks in advance for ur help on this.
Thanks for this post. I implemented this between two weblogic domains and it works. I am facing one problem though: I am able to go from source to destination fine, however, when I go back to source from destination, user gets logged out. It seems jsessionid created by souce gets overwritten by destination. Any ideas would be appreciated.
ReplyDeleteThanks!
Adding to the earlier post.
ReplyDeleteBy making both domains as asserter and relying parties to each other, would I be able to solve the logout issue when sending request back from destination to the source.
Hi Edwin,
ReplyDeleteThanks for the instruction. Although I'm able to complete the test, but I am confused.
My impression is that SAML should enables limiting knowledges of user's identities only on the source site(Domain A), A.K.A ID Provider; the Destination site(Domain B) A.K.A Service Provider should not have all user's identities knowledge, or at least not one to one mapping.
On the orginal post it requires "ssouser" setup on both Doamin A & Domain B,and in your case you have Domain A & B connecting to the same LDAP resource; if I have a domain A user "user1@doamina.com" not exist on domain B, but I want map it to "validate-user" role on domain B, is there any way to do it?
Thanks in advance.
The answer to my own question is: config the "Asserting Party" to allow "virtual user" on the Service Provider side, I have done it and it's working as I expected.
ReplyDeleteThis link contains information I need for configuring the virtual user:
http://www.theserverside.com/news/1369596/SAML-Its-Not-just-for-Web-services
Hi Edwin
ReplyDeleteI am also facing Error 403---Forbidden with SAML authentication.
Can you let me know exactly what I need to check here .
Thanks
Samir
Hi Edwin,
ReplyDeleteI have configured appA and appB onto different servers as mentioned in your existing blog as well as blog from Vikram.
I am able to login to appA and when I click on the link to process to appB, browser is unable to do so with exception
"Firefox can't establish a connection to the server at localhost:7002."
The URL which it is trying to hit is
https://localhost:7002/samlits_ba/its?RPID=rp_00001&TARGET=http://localhost:7003/appB/admin/services.jsp
I have cross-checked my settings. Please let me know if I am missing anything
Edwin, I have two apps App1 and App2 enabled with security but deployed on two managed servers in a single WLS Domain. Now I want to enable SSO between these two apps. In production, we are using OAM. But we are trying on our dev instance. What is the easiest option to enable SSO between our two Apps that are deployed on two different managed servers?
ReplyDeleteHi,
ReplyDeleteI think you don't need to do anything if both apps are working in the same cookie context. the login of the first app is also valid for app2 ( will use a cookie )
thanks
Thanks Edwin. How can I check the cookie context? Some pointers please..
ReplyDeleteEdwin, we tried setting same cookie name, cookie path for two simple web apps and tried to deploy them on two different domains. But cookies are getting over-written and it isn't allowing SSO between those Apps.
ReplyDeleteHi,
ReplyDeleteLast time you had two managed servers in one domain and now you have two domains. This won't work.
But you can try to enable cross domain on both domains and set the same domain passwords .
Thanks
Edwin, I am very sorry. That was a typo in my comment and sorry again for that. Let me rephrase and correct the comment.
ReplyDelete"we tried setting same cookie name, cookie path for two simple web apps and tried to deploy them on two different Managed Servers on a single domain. But cookies are getting over-written and it isn't allowing SSO between those Apps."
Hi Kavin,
DeleteDid you manage to get this working? Stuck with the same issue. Any help is highly appreciated.
Thanks
Hi Kavin,
ReplyDeletecan you try shared sessions between web applications
i think this works with two war in 1 ear.
Enabling Web applications to share the same session
By default, Web applications do not share the same session. If you would like Web applications to share the same session, you can configure the session descriptor at the application level in the weblogic-application.xml deployment descriptor. To enable Web applications to share the same session, set the sharing-enabled attribute in the session descriptor to true in the weblogic-application.xml deployment descriptor. See "sharing-enabled" in session-descriptor.
The session descriptor configuration that you specify at the application level overrides any session descriptor configuration that you specify at the Web application level for all of the Web applications in the application. If you set the sharing-enabled attribute to true at the Web application level, it will be ignored.
All Web applications in an application are automatically started using the same session instance if you specify the session descriptor in the weblogic-application.xml deployment descriptor and set the sharing-enabled attribute to true as in the following example: "sharing-enabled"
memory
true
more in this link https://forums.oracle.com/forums/thread.jspa?threadID=1010819
Oracle Coherence has functionality to enable sharing sessions across WebLogic and other types of java application servers, it's called Coherence*Web.
http://coherence.oracle.com/display/COH35UG/Coherence*Web+Session+Management+Module
http://coherence.oracle.com/display/COH35UG/Coherence*Web+Session+and+Session+Attribute+Scoping
thanks
Hi Edwin,
ReplyDeleteIn my previous post I wrote about the problem I am facing during SAML creation. Let me replicate the requirement.
I am using weblogic as an Identity Provider and Oracle Identity federation (OIF) as a service Provider. The federation will be IDP(weblogic) initiated.
I have configured both sides. I have configured both the sides as per your blog (weblogic and OIF) , published metadata and exchanged.
Now the problem we are facing is that we don’t know that any web application need to be deployed in weblogic or any out of box feature is there in weblogic which we can use in order to get SAML working.
Is there any out of box feature of weblogic by which we can use SAML after configuration only or we need to write a separate java code in order to create login page and using the entire configuration which I made in weblogic.
As my requirement is a bit different from the solution in your blog. I am using OIF as service provider and in your blog weblogic is being used on both the places. I used source site configuration part form the blog (cause I am also using weblogic as an IDP). I configured OIF on my own. Exchanged metadata of OIF and weblogic.
IF I had used OIF at both sides in that case my job would be pretty easy (cause OIF is specifically made for this purpose. But our requirement is different as I have to use weblogic as an IDP).
In your blog you you haven’t written about any web application which needs to be deployed on weblogic side .
What URL I need to hit for SAML if there is out of box feature in weblogic for using SAML(after configuring everything in weblogic).
It’s been so long I am doing this task but I am not able to achieve it. Therefore any help regarding this task will be highly appreciated
Thanks.
Hi Edwin,
ReplyDeleteI have followed your blog and tried to create two domains on a single weblogic server.
When I click the link to navigate to the destination app after logging into the source app, I get the below error:
Firefox can't establish a connection to the server at localhost:7003.
It seems to be a common issue.Can you help me out on this issue.
Thanks,
Deepika
Hi Edwin,
ReplyDeleteI have a task to setup generation of signed SAML token from OSB service using OWSM policy [oracle/wss_saml_token_over_ssl_client_policy], on Weblogic 10.3.6.0. SAML token is getting generated, however is not signed. I have jks keystore configured in "Security Provider Configuration" with self signed certificate. Request advice. Thanks.
thanks.
I have a task to setup generation of signed SAML token from OSB service using OWSM policy [oracle/wss_saml_token_over_ssl_client_policy], on Weblogic 10.3.6.0. SAML token is getting generated, however is not signed. I have jks keystore configured in "Security Provider Configuration" with self signed certificate. Request advice. Thanks.
ReplyDelete